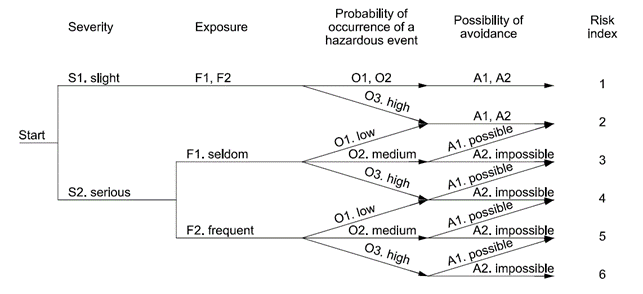
Figure 1 the Risk Graph defined in ISO12100
Risk analysis is an interconnected process that provides a systematic methodology for defining measures or other interventions to protect health in an effective, proportionate and targeted manner. A tool that provides common information for all those who need to perform a risk analysis is the set of ISO standards. ISO stands for “International Organisation for Standardisation”, an organisation responsible for defining the technical standards that an entity must comply with to conform to specific evaluation parameters. The guidelines defined by ISO certifications are voluntary: adherence to them is not required by law, but is necessary to obtain them. These certifications are concerned with certifying the company’s compliance with evaluation criteria to establish the presence of specific elements within the company’s processes.
In the specific case of risk analysis and risk reduction, there is an European legislation that dictates general design principles for machinery safety: ISO 12100. Procedures are described into the text to identify hazards and estimate and assess risks during the relevant phases of the life cycle of the machine, and to eliminate hazards or achieve sufficient sufficiently reduce risks. The strategy for risk assessment and risk reduction described within ISO1200 to be adopted by the designer shows the following actions to be followed:
a) Determine the limits of the machinery, which include the intended use and any reasonably foreseeable misuse thereof: all the phases of the machinery life have to be taken into account. Four types of limits are considered, use limits, space ones, time ones and others, such as properties of the materials to be processed, the environmental ones or the housekeeping;
b) Identify the hazards and associated hazardous situations: the identification must consider every type of event which can occur during all phased of the machine life cycle, as transport, assembly and installation, commissioning, use, dismantling, disabling and scrapping;
c) Estimate the risk for each identified hazard and hazardous situation: After the hazards have been identified in the previous section, a risk estimate must be carried out for each hazardous situation by dangerous situation by determining the risk elements;
d) Evaluate the risk and take decisions about the need for risk reduction: this evaluation exploits the “risk graph” method (Figure 1) based on a decision tree. Each node of the graph represents a risk parameter (severity, exposure, probability of a hazardous situation occurring, possibility of avoiding harm) and each branch of a node represents the class of the parameter. A class must be allocated to each hazardous situation for each parameter. The path on the risk graph then goes from a starting point, which is the severity of the damage, to an end point, which indicates the level or index of risk associated with the combination of classes (branches) that have been chosen. The end result is an estimate of the risk qualified by a number from 1 to 6;
e) eliminate the hazard or reduce the risk associated with the hazard by means of protective measures: Risk reduction can be achieved through the application of inherently safe design principles, the inclusion of protective measures, informative notes in user manuals or the inclusion of Safety Functions.
Another document (not a standard yet, but a technical annex of ISO12100) that is considered essential for analysing the security of a machine is ISO/TR 22100-4, which provides guidelines for cybersecurity aspects. This annex provides fundamental information for identifying and dealing with cyber threats that can affect the safety of machinery. ISO 12100 does not explicitly address IT-security attacks and/or threats which are categorized as intentional abuse and criminal acts. However, manufacturers providing machinery which can have vulnerabilities to IT-security attacks and/or threats should take this aspect into account especially when IT-security attacks and/or threats can have an impact to safety of machinery.
ISO12100 allows to perform a risk assessment based on defined limits and intended use of the machine, therefore in the safety field, while these guidelines for cybersecurity aspects allow to consider security risks to the machine caused by a threat which can succeed or exploit a vulnerability (e.g., interface, introduces software virus) to cause damages. The potential responses to security risks should apply the following hierarchy based on ISO 12100:
a) eliminate the security risk by design (avoid vulnerabilities);
b) mitigate the security risk by risk reduction (mitigation) measures (limit vulnerabilities);
c) provide information about the residual security risk and the measures to be adapted by the user.
In VALU3S project, recommendations of ISO12100 and its technical annex have been analysed and implemented in the algorithms of RAMSES tool, allowing risk assessment and mitigation process for autonomous machines. In fact, RAMSES is a Risk Assessment software for the verification and the validation of automated system. It supports the user (ideally, the machine designer o the safety engineer) in identifying main hazards and risks related to machinery components and process, as well as to the operations carried out by human workers. Furthermore, once risk scenarios are identified RAMSES allows the user to find proper safety measures and understand the consequent reduction of risks.
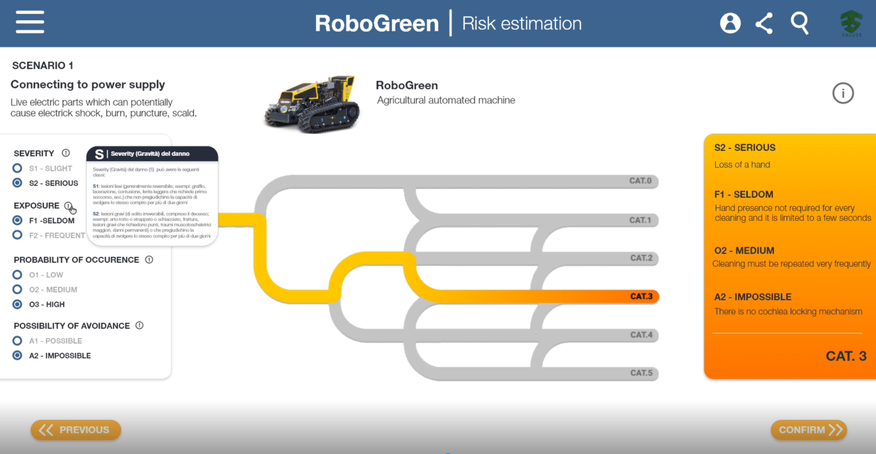
Figure 2 Screen RAMSES – Risk Analysis
Indeed, RAMSES enhances safety and security of automated systems themselves, as well as of people and other elements interacting with them, through the spread of validated reliable products into several market domains.

Miss Deborah Hugon is graduated in Safety Engineering for Transport, Logistics and Production at the University of Genova. Her knowledge is also in the civil and environmental engineering area since she has a bachelor’s degree in this field. In her master thesis, she studied the dynamic programming algorithm applied to maritime transport. Now in STAM she is working on European projects in the field of security simulating the users’ behavior in critical infrastructures and developing risk assessment.
