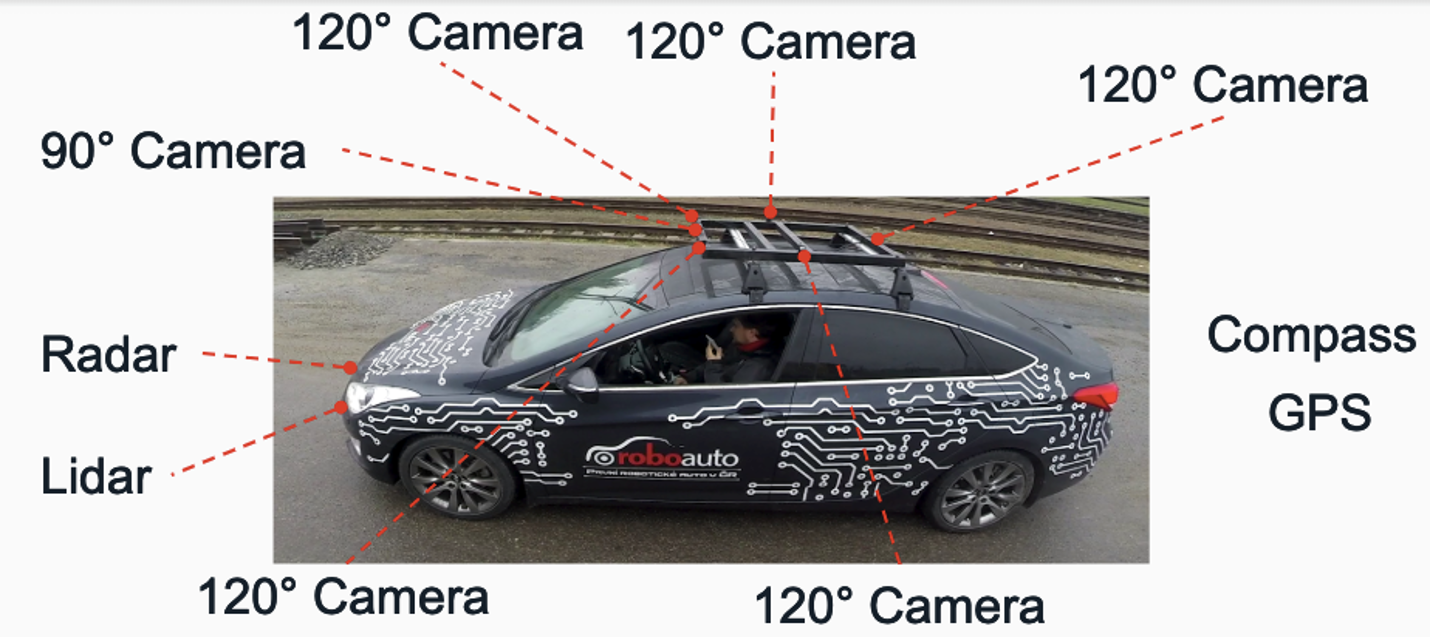
Use Case 2 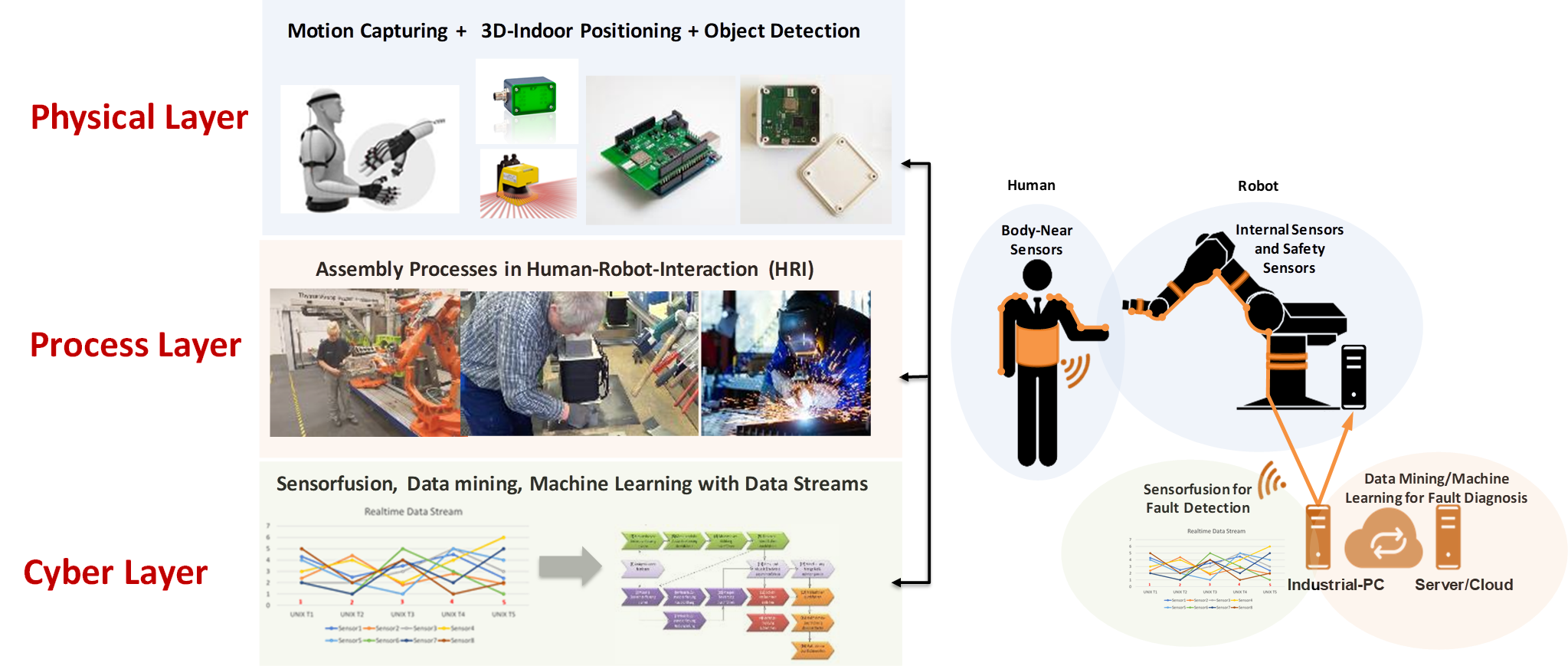
Use Case 4 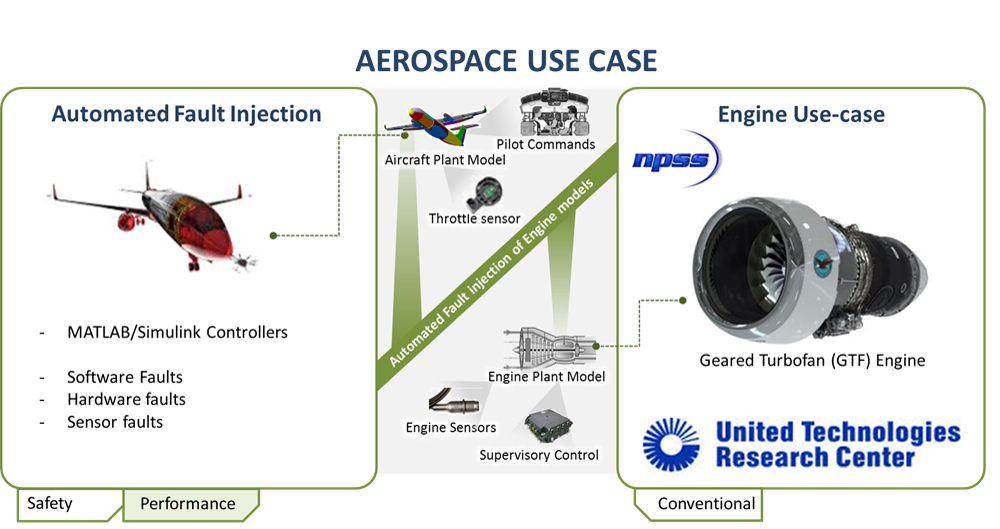
Use Case 5 
Use Case 6 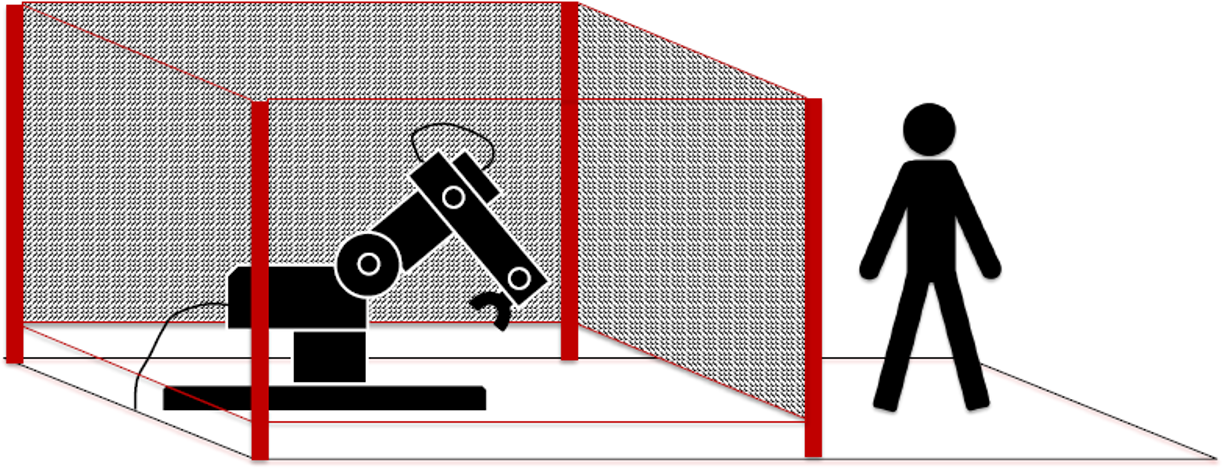
Use Case 7 
Use Case 8 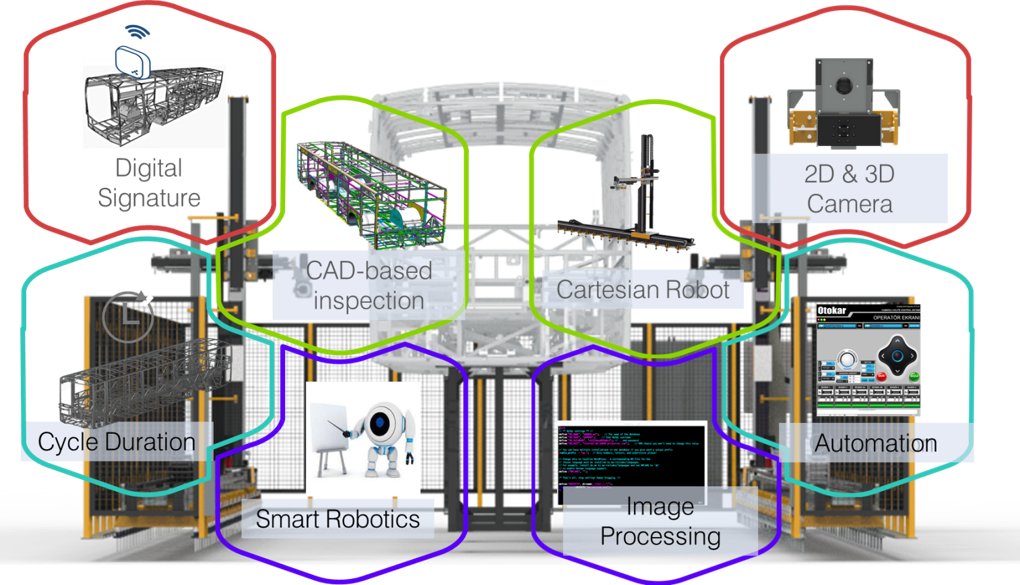
Use Case 11 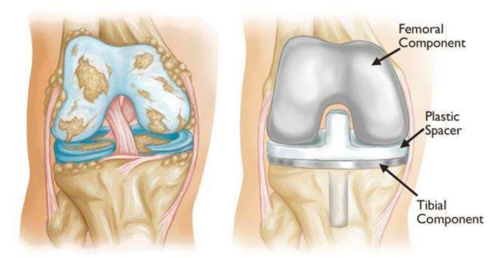
Use Case 12 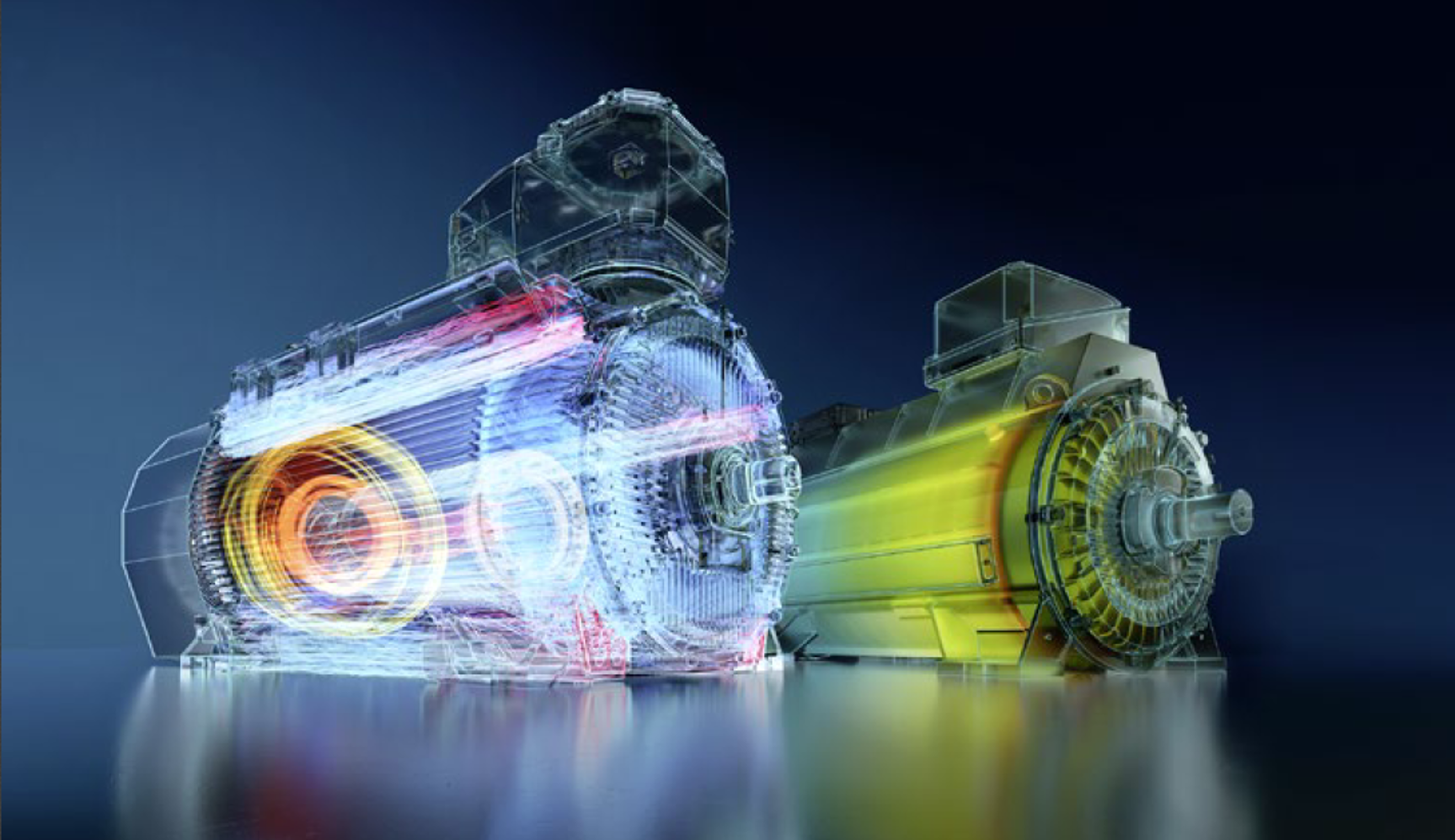
Use Case 13
Recent News
 VALU3S Use Case Interview: Autonomous Train Operation.
VALU3S Use Case Interview: Autonomous Train Operation. VALU3S Use Case Interview: V&V of driver monitoring system to guarantee its safety and performance
VALU3S Use Case Interview: V&V of driver monitoring system to guarantee its safety and performance VALU3S Use Case Interview: Collaboration in a NMT Infusion Controller for regulation of NeuroMuscular Transmission Vital Sign in Operating Room.
VALU3S Use Case Interview: Collaboration in a NMT Infusion Controller for regulation of NeuroMuscular Transmission Vital Sign in Operating Room. VALU3S Use Case Interview: Industrial Drives for Motion Control
VALU3S Use Case Interview: Industrial Drives for Motion Control VALU3S Use Case Interview: Intelligent Traffic Surveillance
VALU3S Use Case Interview: Intelligent Traffic Surveillance
Recent blog posts
 Using Simulator for testing autonomous drive
Using Simulator for testing autonomous drive Virtual Stress-Testing a Digital Twin of a Motor Control Platform using Dynamic Fault-injection
Virtual Stress-Testing a Digital Twin of a Motor Control Platform using Dynamic Fault-injection Knowledge-centric systems engineering with the Systems Engineering Suite
Knowledge-centric systems engineering with the Systems Engineering Suite Applying a “Machine Learning Pipeline” to detect unknown faults and failures in a Human Robot Interaction assembly process
Applying a “Machine Learning Pipeline” to detect unknown faults and failures in a Human Robot Interaction assembly process ISO12100 Standard: how Risk Analysis contributes to design of safe machinery
ISO12100 Standard: how Risk Analysis contributes to design of safe machinery
Archives
- September 2023
- July 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- December 2020
- November 2020
- September 2020
- August 2020
- April 2020
